Security Inspection Overview
Security inspection is a feature that examines the cloud infrastructure drawn on the canvas for potential security issues before final export. It helps users identify human errors and vulnerabilities that may pose security risks.
To perform a security inspection, please follow the steps below.
Savethe canvas.- Click on
Tools > Vulnerability Inspection. - Check the
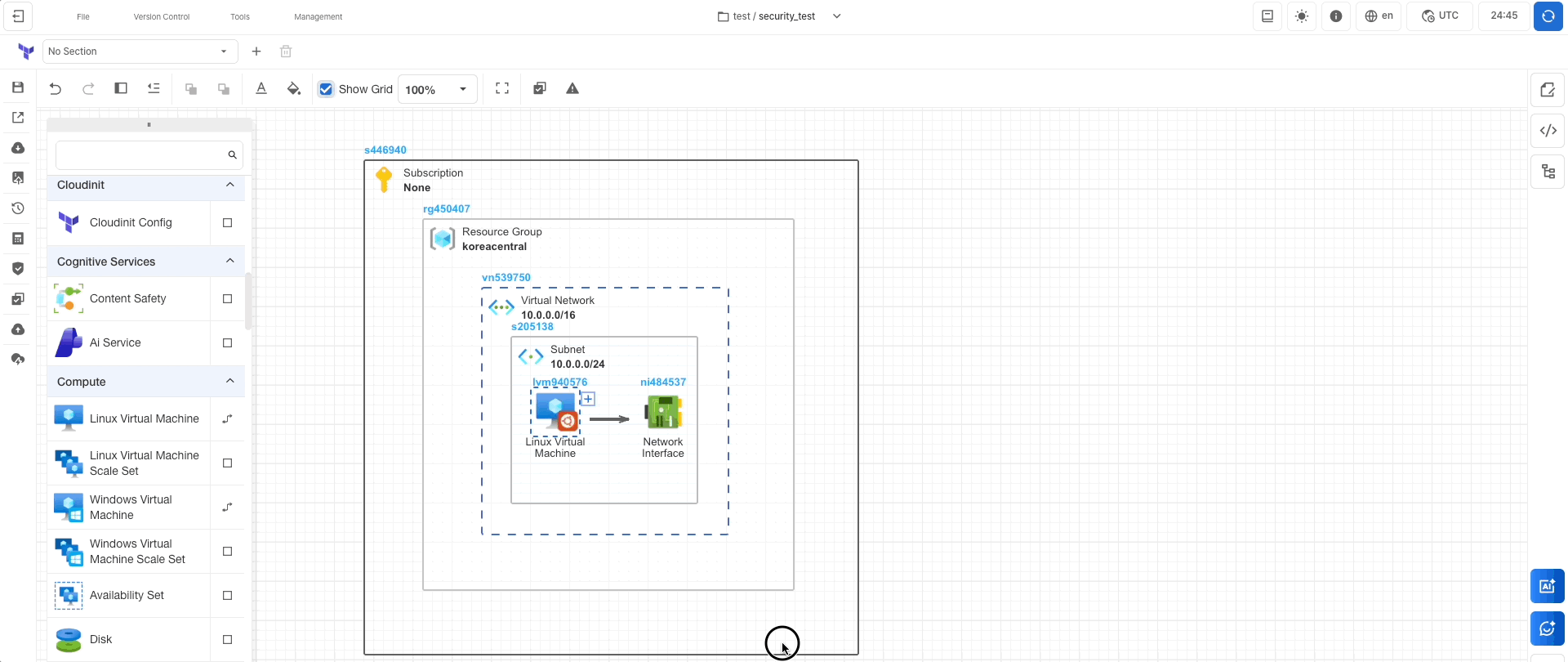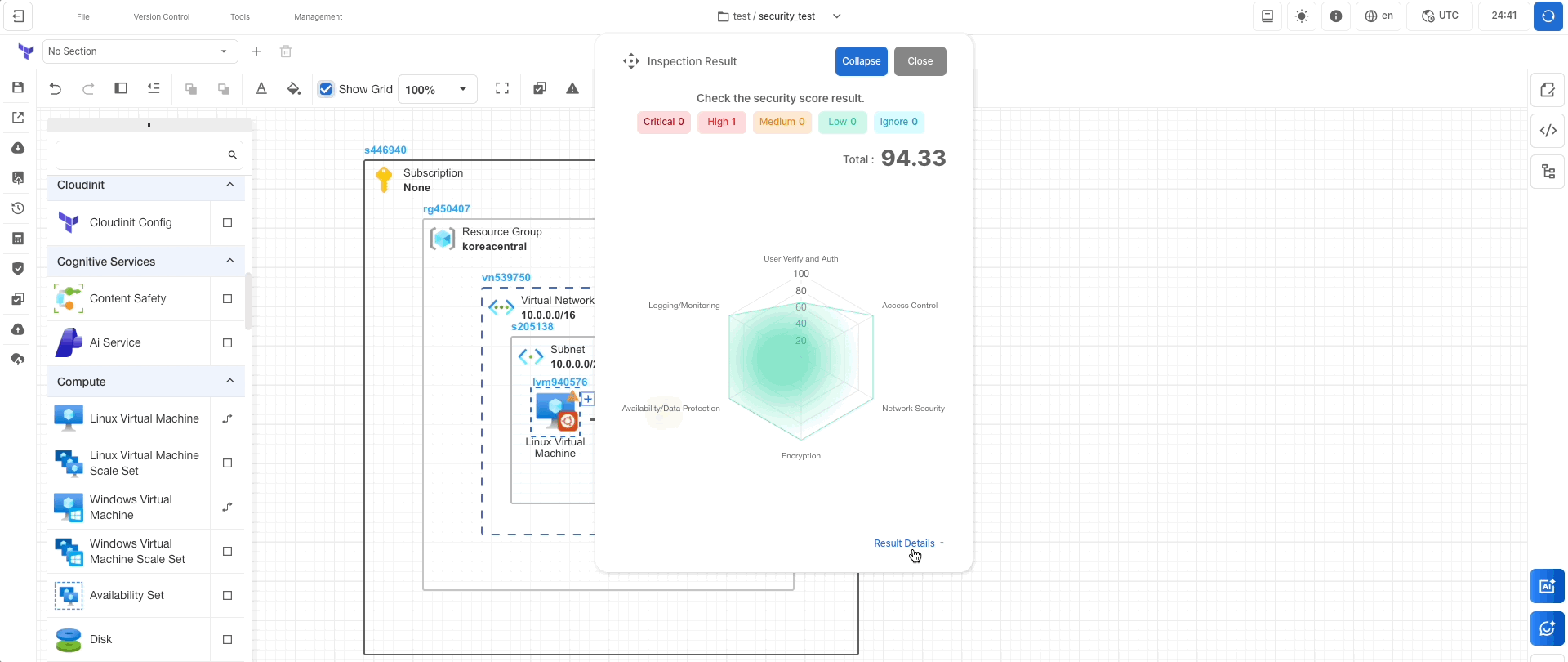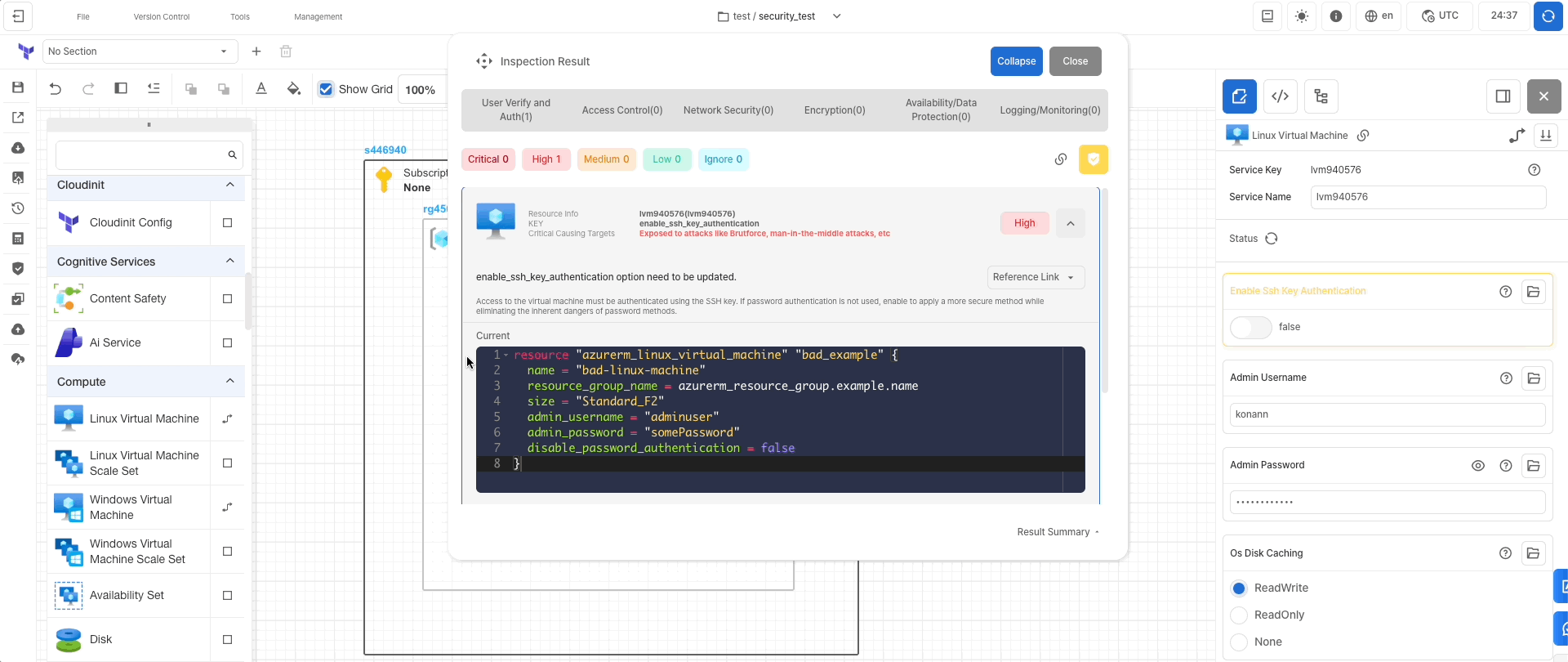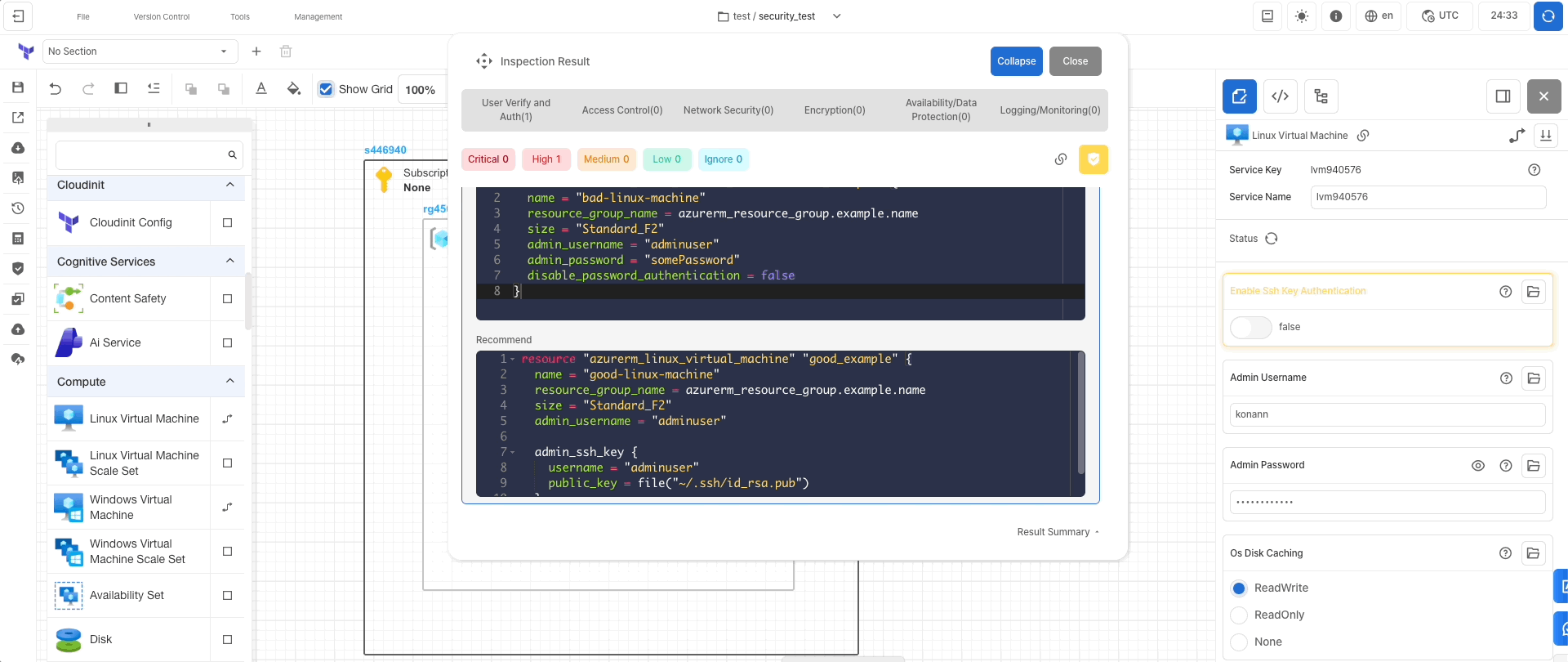
Inspection Score Resultsin the detailed results. - Click
View Detailsto examine the resources associated with each stage. - To modify the infrastructure, locate services marked as
Riskyor `High on the right side. - If a service is found, click the
Arrow Iconto view resolution suggestions.Current Codeshows the existing canvas code, whileRecommended Codedisplays code with recommended security improvements. - Close the security inspection window and make the necessary adjustments on the canvas.
Security Threat Levels
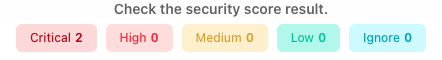
Security threat levels are categorized into five stages: Critical, Warning, Moderate, Low, and Good.
The number next to each stage represents the number of resources corresponding to that level. For example,
if the Critical level shows a number 1, it means there is 1 resource with a critical security issue in the current canvas.
While it's advisable to address resources in the Critical and High categories, it is not mandatory. To view the resources associated with each stage, click View Details.
| Security Threat Level | Description |
|---|---|
| Critical | The security status is highly vulnerable. It's recommended to revise the code if it's a critical infrastructure component. |
| Warning | The security status is weak. It's advisable to update the code if it's an important infrastructure component. |
| Moderate | The security status is average. |
| Low | The security status is good. |
| Good | The security status is safe. It is acceptable to proceed with deployment. |
Security Check Items
CloudStudio provides six security check items to ensure compliance with security standards.
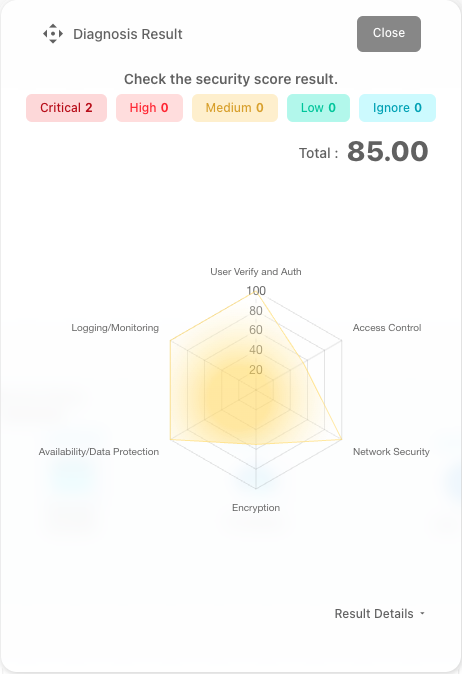
| Security Check Item | Description |
|---|---|
| User Authentication & Authorization | Shows items related to user identification and authentication. |
| Access Control | Displays items related to system access control. |
| Network Security | Shows items related to network security. |
| Data Protection | Displays items related to backup and data security. |
| Logging & Monitoring | Shows items related to logging and monitoring. |
| Encryption | Displays items related to data encryption. |